Cyber Kill Chain: 7 stages of a cyber attack
Cyber Kill Chain is a framework that tells us how an attack is executed. This model can also be used to build a good cyber security program. This attack chain help us understand how Advance Persistence Threats (APT), Ransomware, security breaches, etc get into our network and how we can fight them at different stages.
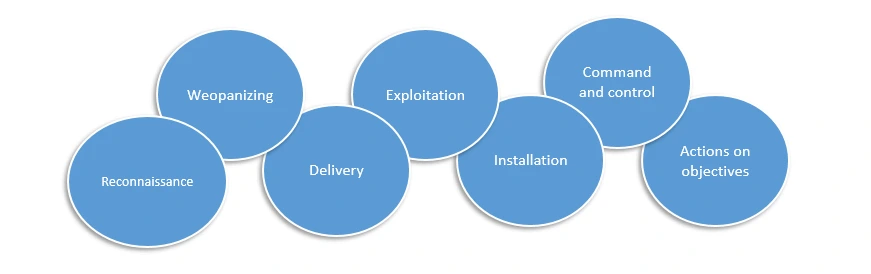
There are 7 such stages in which a cyber attack can be segmented, these stages form the Cyber Kill Chain.
Let’s have a look at these 7 stages:
- Reconnaissance: This is the information gathering stage. In this, the attacker assesses the situation from the outside of the target. The attacker could use active and passive ways to gather information like email addresses, conference informations, internal management shuffling, etc..
Under Active scan, the attacker typically uses NMAP, vulnerability scanners, banner grabbing, etc. tools which could be detected.
Under Passive scan, attackers use information available publicly like job postings, news, SHODAN , whois, etc.
Basically the motive of this stage is to gather information which could help in exploiting weaknesses. - Weaponizing: This is the stage where the attacker chooses which method should be used to deliver the exploit. For example, an attacker has gathered some email addresses of employees of XYZ inc. He decides that he will use phishing emails or malicious attachments to target the organisation.
The cyber security team of the company can disable office macros, javascript enabled browser plugins, email security softwares, multi-factor authentication, audit logging to prepare in advance for such attacks. - Delivery: This is the stage when the attacker delivers the exploit to the target. This is where the attacker decides which avenue to deliver the exploit. For example, the attacker has made a malicious .docx file and he decides to send it in a email with the subject of “Post salary cut revised CTC” or something like that. This can trigger an emotional response in the victim and he might, without paying attention if the email is from legitimate source, open the document and can get compromised.
The security team can provide user awareness training for such triggering attackes, they can also launch phishing campaigns, use IPS/IDS, web filtering, DNS filtering, etc. - Exploitation: After the successful delivery of the payload, attacker can choose to exploit the weakness anytime he/she wishes. For example, remote code execution, javascript exploitation, SQL injection, buffer overflow, RATs, etc. The ultimate goal of this stage is to gain access to the system.
Defensive measure against this could be installing anti-malware tools, anti-exploits, data execution prevention(DEP), sandbox to open files, etc. - Installation: This is a stage where the attacker tries to inject payload further into the system to maintain Persistence. This could be done by DLL hijacking, meterpreter, RAT, registry changes, powershell commands, etc.
To defend against this, security teams can use endpoint detection and response(EDR), disable powershell, chroot on linux, follow incidence response SOPs, isolating infected system, restore/reimage, etc. - Command and Control: This is the stage where the attacker has remote control of the target system. Attacker usually stays low profile to prevent being detected. An attacker would even stay silent for 5 months and the target might not even know about it.
To stay protected from such persistence, organizations should use next-gen firewalls, DNS redirects, application controls, network segmentation, look for IOCs consistently etc. - Actions on Objectives: We can say this is the ultimate motive of an attacker. This could be anything like political, financial, malicious insider, espionage, or anything just like that. For example: spying on competitors data.



