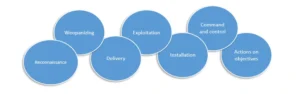
What is Ransomware? Defend against ransomware.
Ransomware is a kind of software which holds system/systems hostage for money (usually cryptocurrency like bitcoin). Once the ransom is paid, victim is provided with a “key” to unlock the affected systems. Ransomware holds the system by encrypting victim’s files. This can cause significant dent on business’s operation as the encrypted files are often critical….